Security Analysis of the VoIP (Voice Over Internet Protocol) System
DOI:
https://doi.org/10.63876/ijss.v1i3.69Keywords:
VoIP security, SRTP, DoS attack, intrusion detection, session hijacking, network securityAbstract
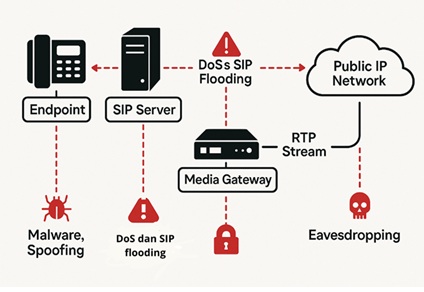
Voice over Internet Protocol (VoIP) is a communication technology that enables voice transmission over IP-based networks, offering advantages such as cost efficiency, flexibility, and service integration. Despite its benefits, VoIP faces significant security vulnerabilities due to its open architecture and dependence on public internet infrastructure. This study presents a literature-based analysis of the primary security threats targeting VoIP systems, including eavesdropping, Denial of Service (DoS) attacks, spoofing, session hijacking, and Network Address Translation (NAT) traversal problems. The research also discusses a range of countermeasures, including Secure Real-time Transport Protocol (SRTP), Transport Layer Security (TLS), Intrusion Detection and Prevention Systems (IDS/IPS), adaptive firewalls, and robust authentication protocols such as STIR/SHAKEN. While these technical solutions are effective, their success depends on proper implementation and continuous system monitoring. Although there may be minor trade-offs in performance, particularly in latency, such compromises are acceptable under global standards to ensure secure communication. The findings underscore the importance of a layered security strategy that maintains both protection and Quality of Service (QoS), making VoIP a dependable solution for critical sectors such as government, finance, and business.
Downloads
References
S. S. M. Saqquaf, P. Bhagyalakshmi, S. M. Shruti, B. M. Varsha, and S. Araballi, “Dynamically Automated Interactive Voice Response System for Smart city Surveillance,” 2016 IEEE Int. Conf. Recent Trends Electron. Inf. Commun. Technol. RTEICT 2016 - Proc., pp. 1176–1180, 2017, doi: https://doi.org/10.1109/RTEICT.2016.7808017.
P. Hoole and S. Hoole, Lightning Engineering: Physics, Computer-based Test-bed, Protection of Ground and Airborne Systems. 2022. doi: https://doi.org/10.1007/978-3-030-94728-6.
A. M. Ramly, Z. W. Ng, Y. Khamayseh, C. S. C. Kwan, A. Amphawan, and T. K. Neo, “Review and Enhancement of VoIP Security: Identifying Vulnerabilities and Proposing Integrated Solutions,” J. Telecommun. Digit. Econ., vol. 12, no. 4, pp. 109–136, 2024, doi: https://doi.org/10.18080/jtde.v12n4.1022.
M. M. Huda, Keamanan Informasi. 2020.
J. Liang, S. Chen, Z. Wei, S. Zhao, and W. Zhao, “HAGDetector: Heterogeneous DGA domain name detection model,” Comput. Secur., vol. 120, p. 102803, Sep. 2022, doi: https://doi.org/10.1016/j.cose.2022.102803.
C. Cuevas, R. Martínez, D. Berjón, and N. García, “Detection of Stationary Foreground Objects Using Multiple Nonparametric Background-Foreground Models on a Finite State Machine,” IEEE Trans. Image Process., vol. 26, no. 3, 2016.
H. Sinnreich and A. B. Johnston, Using SIP Henry Sinnreich. 2012.
D. Stuttard and M. Pinto, The Web Application Hacker’s Handbook: Finding and Exploiting Security Flaws, vol. 7. 2011.
R. Punna, G. Aravamuthan, and S. Kar, “Recovering 3D from 2D Image Points (Calibrated Camera Approach for Surveillance),” in 2022 IEEE 7th International conference for Convergence in Technology, I2CT 2022, 2022. doi: https://doi.org/10.1109/I2CT54291.2022.9825444.
D. Azizi and V. Arinal, “Sistem Monitoring Daya Listrik Menggunakan Internet of Thing (Iot) Berbasis Mobile,” J. Indones. Manaj. Inform. dan Komun., vol. 4, no. 3, pp. 1808–1813, 2023, doi: https://doi.org/10.35870/jimik.v4i3.409.
C. Chen, “Combining quality of services path first routing and admission control to support VoIP traffic,” Futur. Gener. Comput. Syst., vol. 29, no. 7, pp. 1742–1750, 2013, doi: https://doi.org/10.1016/j.future.2012.03.026.
F. D. Silalahi, “Keamanan Cyber (Cyber Security),” Penerbit Yayasan Prima Agus Tek., pp. 1–285, 2022.
J. Jokinen, T. Latvala, and J. L. M. Lastra, “Integrating smart city services using Arrowhead framework,” IECON Proc. (Industrial Electron. Conf., pp. 5568–5573, 2016, doi: https://doi.org/10.1109/IECON.2016.7793708.
H. Hsieh, J. Chen, A. Benslimane, and C. Applications, “5G Virtualized Multi-access Edge Computing Platform for IoT Applications,” 2018, doi: https://doi.org/10.1016/j.jnca.2018.05.001.This.
A. Patil, S. Yadav, and M. Pandey, “Exploring Emerging Trends in AI-Driven Technological Advancements,” Int. J. Technol. Model., vol. 3, no. 3, pp. 138–151, Dec. 2024, doi: https://doi.org/10.63876/ijtm.v3i3.140.
A. V Savchenko, “Maximum-likelihood approximate nearest neighbor method in real- time image recognition,” Pattern Recognit., vol. 61, pp. 459–469, 2017, doi: https://doi.org/10.1016/j.patcog.2016.08.015.
T. M. Đức and N. T. Hương, “Improvement of Vehicle detection and classification performance with Region of Interest,” ITEJ (Information Technol. Eng. Journals), vol. 8, no. 1, pp. 34–41, Jul. 2023, doi: https://doi.org/10.24235/itej.v8i1.116.
K. Biswas and V. Muthukkumarasamy, “Securing smart cities using blockchain technology,” Proc. - 18th IEEE Int. Conf. High Perform. Comput. Commun. 14th IEEE Int. Conf. Smart City 2nd IEEE Int. Conf. Data Sci. Syst. HPCC/SmartCity/DSS 2016, pp. 1392–1393, 2017, doi: https://doi.org/10.1109/HPCC-SmartCity-DSS.2016.0198.
A. A. Simiscuka, “A Networking Scheme for an Internet of Things Integration Platform,” 2017 IEEE Int. Conf. Commun. Work. (ICC Work., pp. 271–276, 2017, doi: https://doi.org/10.1109/ICCW.2017.7962669.
G. L. Foresti, L. Marcenaro, and C. S. Regazzoni, “Automatic detection and indexing of video-event shots for surveillance applications,” IEEE Trans. Multimed., vol. 4, no. 4, pp. 459 – 471, 2002, doi: https://doi.org/10.1109/TMM.2002.802024.
H. Badan and G. Indonesia, “Rancangan Pengem bangan Sistem Layanan Diseminasi Peringatan Dini Tsunam i Berbasis Service Oriented Architecture ( SOA ) ( Studi kasus : Badan M eteorologi Klim atologi dan Geofisika ),” vol. 02, no. 03, pp. 230–243, 2019.
S. T. Kouyoumdjieva, P. Danielis, and G. Karlsson, “Survey of Non-Image-Based Approaches for Counting People,” IEEE Commun. Surv. Tutorials, vol. 22, no. 2, pp. 1305–1336, 2020, doi: https://doi.org/10.1109/COMST.2019.2902824.
F. Porikli, Y. Ivanov, and T. Haga, “Robust abandoned object detection using dual foregrounds,” EURASIP J. Adv. Signal Process., vol. 2008, 2008, doi: https://doi.org/10.1155/2008/197875.